Before You Begin
Before beginning this guide, you should have:Explore Your Data
In Honeycomb, you can slice and dice your data from your Home view, or create Boards to save relevant queries and visualizations. Either way, you will want to leverage Honeycomb’s features to create Triggers and explore outliers using BubbleUp and Correlations.Slice and Dice Your Data
Once you have log data in Honeycomb, navigate to the Home view and select your log dataset to begin exploring your data. The Logs view contains visualizations specially designed for exploring log data.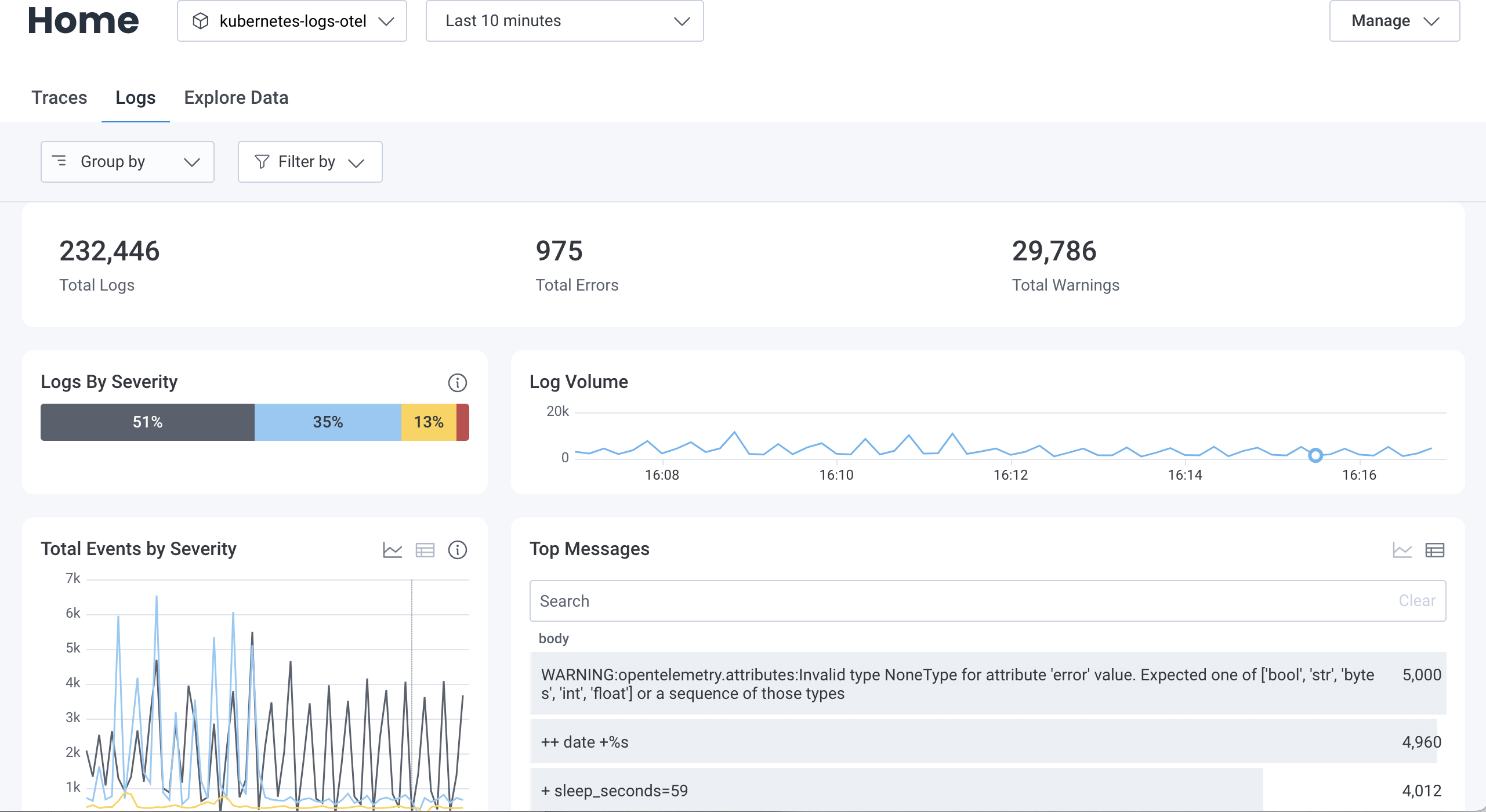
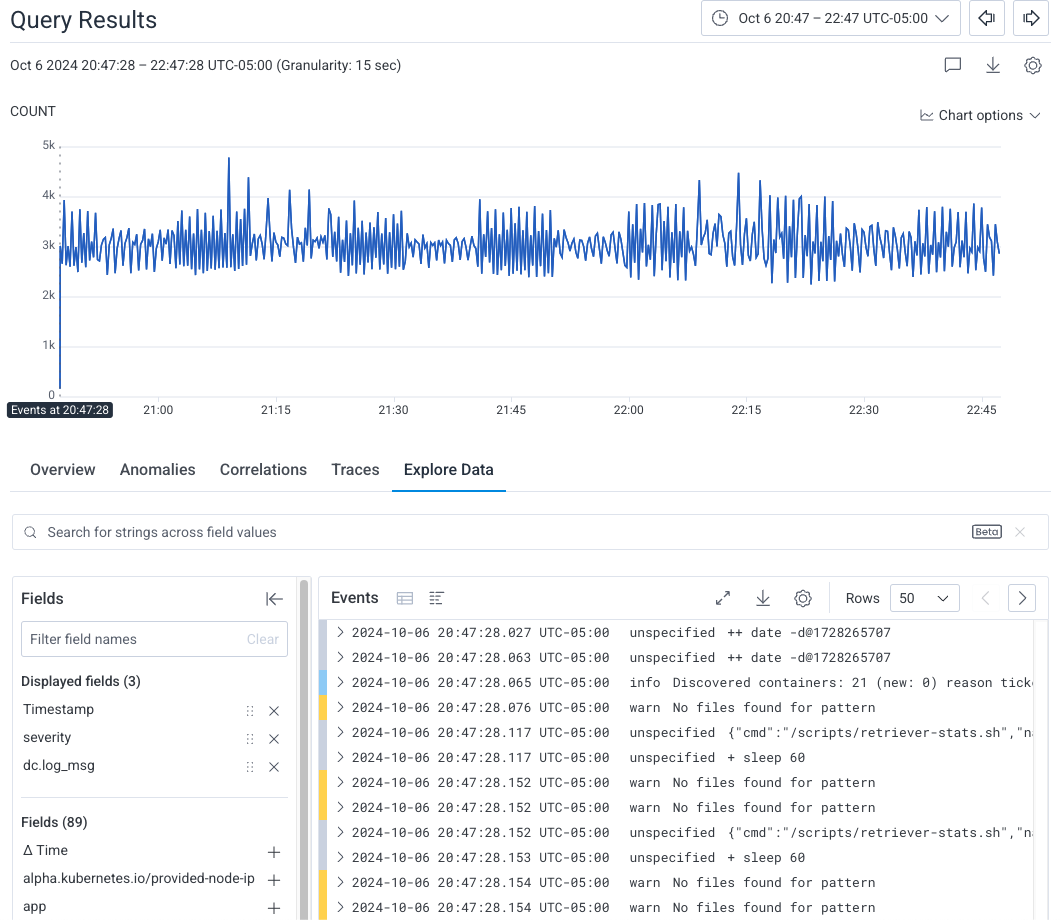
Create a Board
For quick reference over time, you should create a Board that you can customize to show log-specific items of interest.Create Triggers
Once you have created a Board, you will likely want to configure some Triggers, so you can receive notifications when your data in Honeycomb crosses defined thresholds. To create a Trigger:- On your Board, locate a Query from which you want to create a Trigger.
- Select the query to open it in the Query Builder display.
- Select the three-dot overflow menu, located to the left of Run Query, and select Make Trigger.
- Configure the trigger by defining trigger details, an alert threshold, and your notification preferences.
Investigate Unusual Behavior
Simplify debugging by using the core analysis loop—Honeycomb BubbleUp, Correlations, and rich queryable data—to dig in to application behavior.Identify Commonalities in Structured Logs
Examine what a subset of logs might have in common using BubbleUp.Scenario:
You have structured MySQL slow query logs and want to discover specific queries that are running slower than expected.Solution:
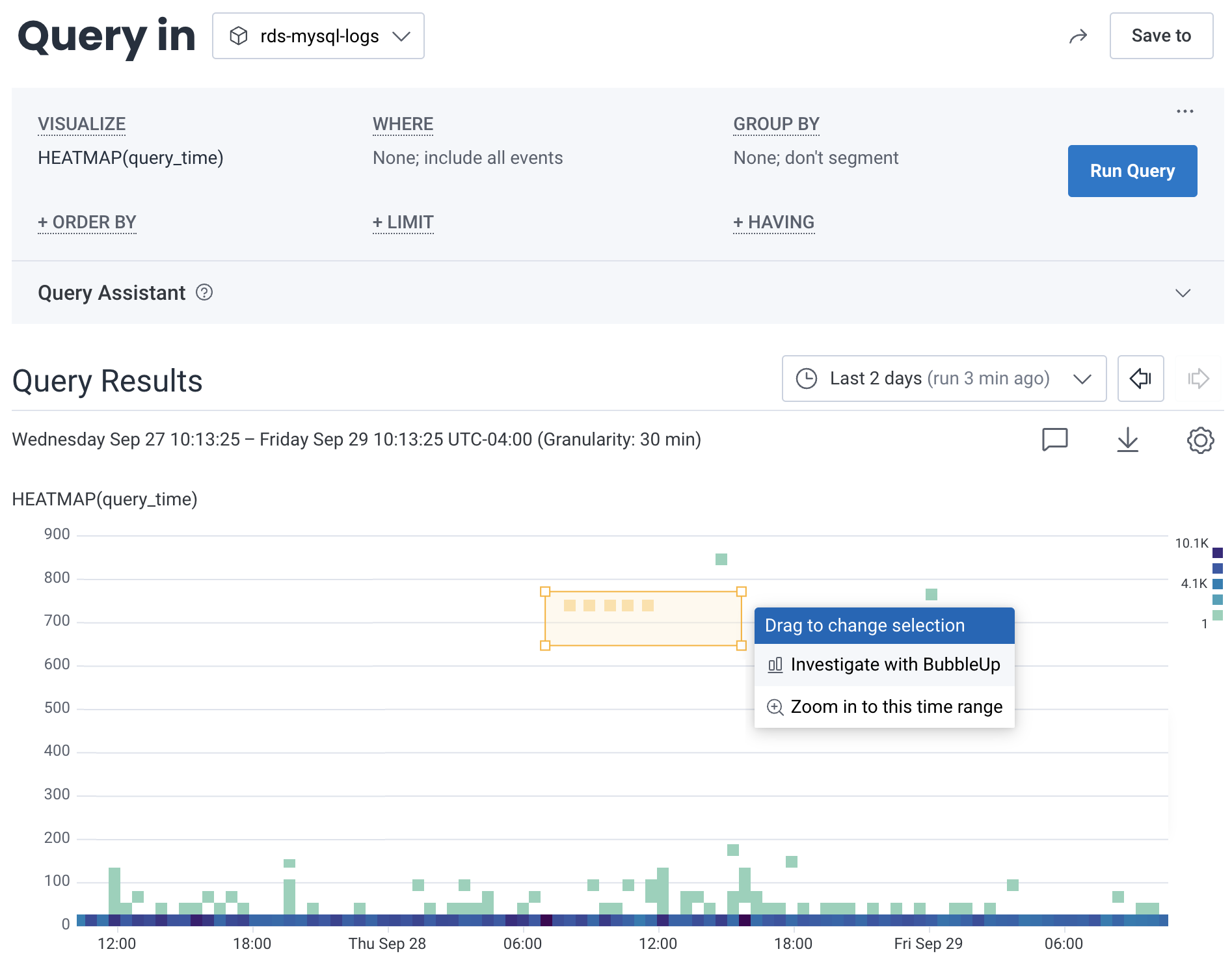
Run a query that visualizes a heatmap on
query_time, then use BubbleUp to identify similarities between the slow queries.- Navigate to the Query Builder.
-
Build the following query:
VISUALIZE HEATMAP(query_time) - Select Run Query.
- In the Query Results section, locate the heatmap, and draw a box around logs that have a longer duration than you prefer.
-
From the context menu, select BubbleUp Outliers.
-
Locate the BubbleUp view, and use the charts to examine the attributes that that logs inside your selection have in common.
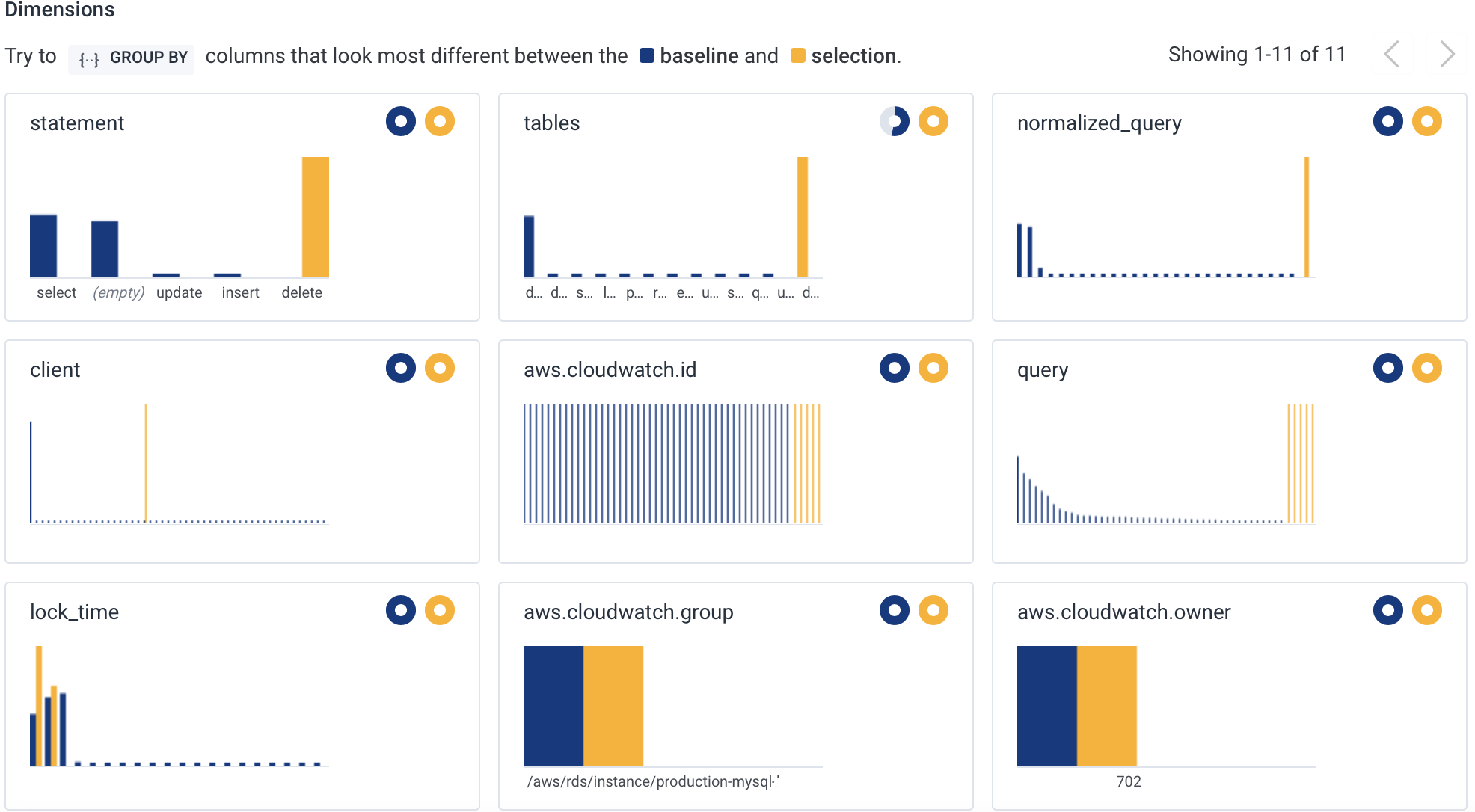
statement chart—each of the problematic logs contains the same DELETE statement.
You can now use the normalized_query chart to see the exact shape of the query that you need to optimize.Parse Unstructured Logs
Because of the shape of unstructured log data in Honeycomb, unstructured logs can be hard to query. To improve the experience and make unstructured logs more useful, use calculated fields to parse meaningful information out of themessage attribute.
- Create a calculated field.
-
Leverage the
REG_VALUEoperation to parse log data using regular expressions.