The Splunk HTTP Event Collector source can be used to receive events (logs) from applications that emit events in the Splunk HEC format. Events are converted to OTLP format and can be sent to any destination.
The HEC source can be combined with the Splunk HEC Destination. This allows Telemetry Pipeline’s agent to sit in the middle of a Splunk pipeline, giving you the ability to leverage Telemetry Pipeline’s processing capabilities.
| Platform | Metrics | Logs | Traces |
|---|---|---|---|
| Linux | ✓ | ||
| Windows | ✓ | ||
| macOS | ✓ | ||
| Kubernetes Gateway | ✓ |
| Parameter | Type | Default | Description |
|---|---|---|---|
| listen_port | int |
8888 | Port to listen on. |
| listen_ip | string |
“0.0.0.0” | IP Address to listen on. |
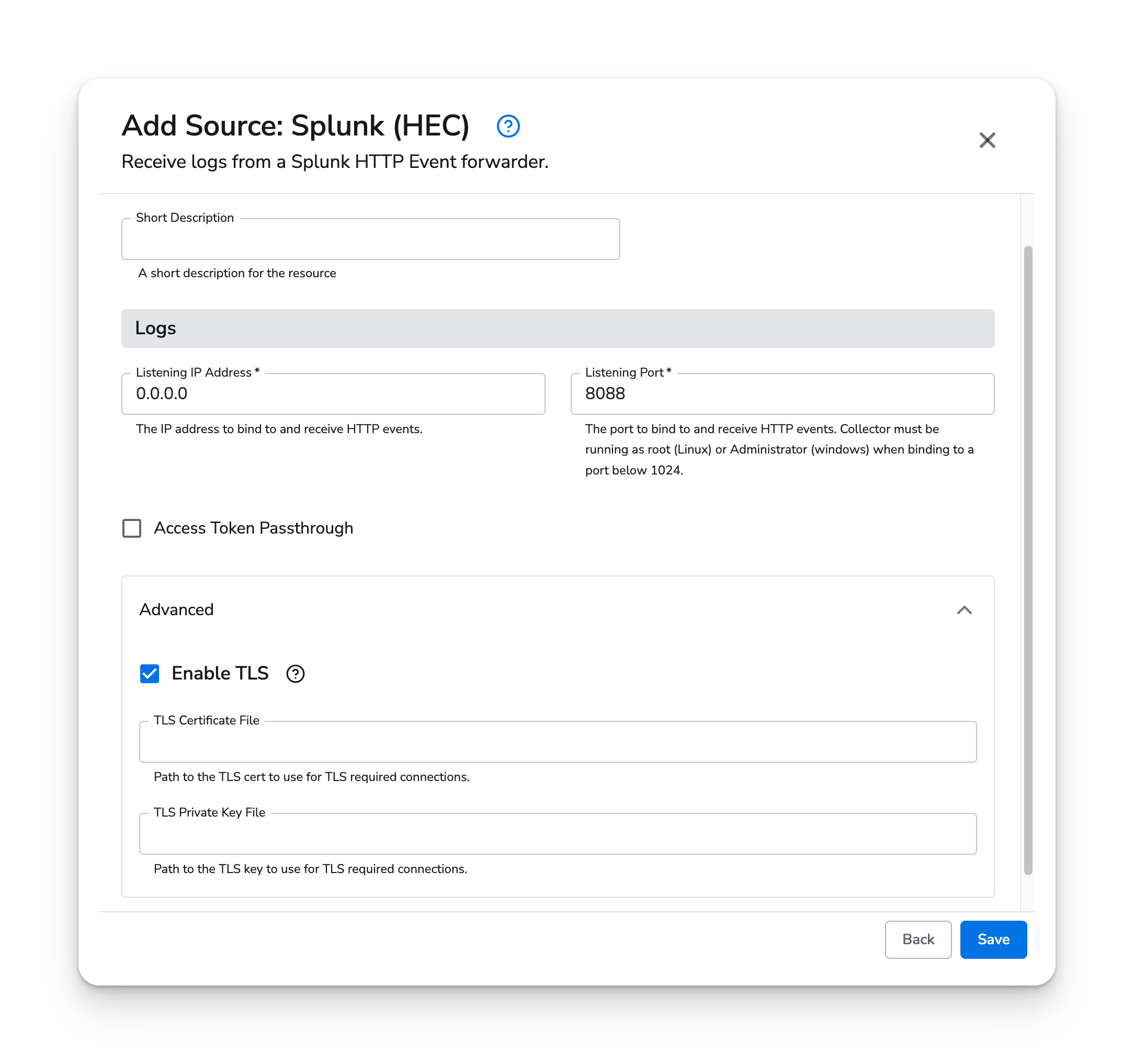
| access_token_passthrough | string |
false | Whether to preserve incoming access token (Splunk header value) as “com.splunk.hec.access_token” metric resource label. |
| enable_tls | bool |
false | Whether or not to use TLS. |
| tls_certificate_path | string |
Path to the TLS cert to use for TLS-required connections. | |
| tls_private_key_path | string |
Path to the TLS key to use for TLS-required connections. |
The HEC source type has two required parameters:
It is recommended to enable the Access Token Passthrough option if you wish to preserve the Splunk access token header as a resource attribute com.splunk_hec.access_token.
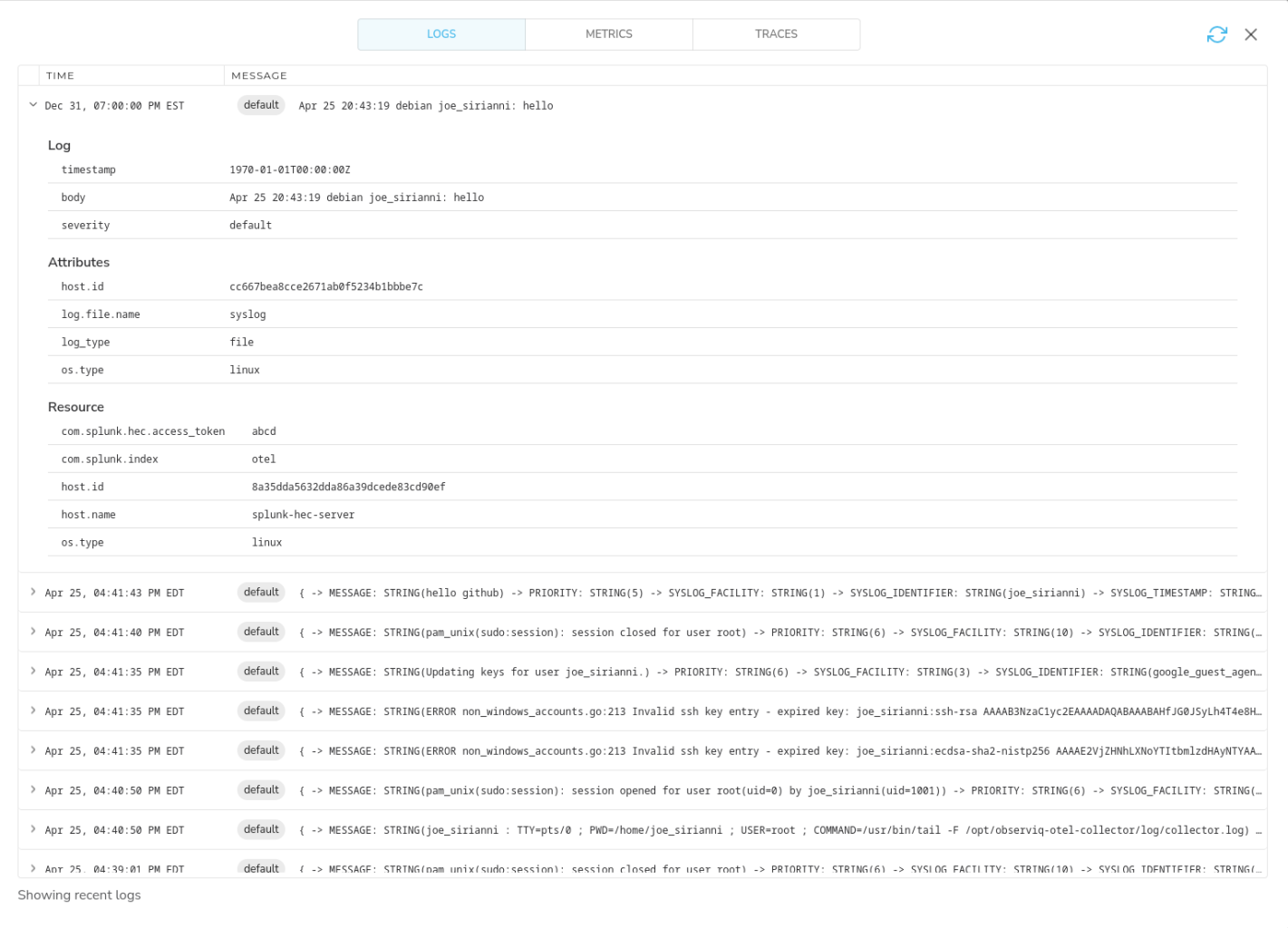
Once configured, incoming events will be displayed as logs like this:
The Splunk HEC source type supports Kubernetes Gateway agents. Splunk HEC forwarders can send logs to the agents using the clusterIP services.
Add the Splunk HEC source to your Gateway agent configuration. Set “Listen Address” to 0.0.0.0 and
Listen Port to 8088.
The Splunk forwarders should be configured to forward telemetry to bindplane-gateway-agent.bindplane-agent.svc.cluster.local
on port 8088. If the Splunk forwarders live outside of the cluster, you must make the bindplane-gateway-agent
service in the bindplane-agent namespace available using TCP ingress or by defining your own service
that can receive traffic from outside of the cluster. See the Kubernetes service documentation for more information.