This feature is available as an add-on for the Honeycomb Enterprise plan.
Please contact your Honeycomb account team for details.
Description
The Honeycomb Telemetry Pipeline (HTP) Gateway source is an OTLP source meant to be used for gateway nodes. When using this source in conjunction with an HTP Gateway destination from another configuration, telemetry traveling through this source will not be double counted in the Summary view.Supported Platforms
| Platform | Metrics | Logs | Traces |
|---|---|---|---|
| Linux | ✓ | ✓ | ✓ |
| Windows | ✓ | ✓ | ✓ |
| macOS | ✓ | ✓ | ✓ |
| Kubernetes Node (DaemonSet) | ✓ | ✓ | ✓ |
| Kubernetes Gateway | ✓ | ✓ | ✓ |
| OpenShift 4 Node (DaemonSet) | ✓ | ✓ | ✓ |
Configuration Table
| Parameter | Type | Default | Description |
|---|---|---|---|
| telemetry_types | telemetrySelector | ["Logs", "Metrics", "Traces"] | Choose Telemetry Type. |
| listen_address | string | ”0.0.0.0” | The IP address to listen on. |
| grpc_port | int | 4317 | TCP port to receive OTLP telemetry using the gRPC protocol. The port used must not be the same as the HTTP port. Set to 0 to disable. |
| http_port | int | 4318 | TCP port to receive OTLP telemetry using the HTTP protocol. The port used must not be the same as the gRPC port. Set to 0 to disable. |
| enable_tls | bool | false | Whether or not to use TLS. |
| insecure_skip_verify | bool | false | Enable to skip TLS certificate verification. |
| ca_file | string | Certificate authority used to validate the database server’s TLS certificate. | |
| cert_file | string | A TLS certificate used for client authentication if mutual TLS is enabled. | |
| key_file | string | A TLS private key used for client authentication if mutual TLS is enabled. |
Example Configuration
The HTP Gateway source type does not have any required fields. By default, the HTP Gateway source will listen on ports 4317/gRPC and 4318/HTTP on all IP addresses without TLS.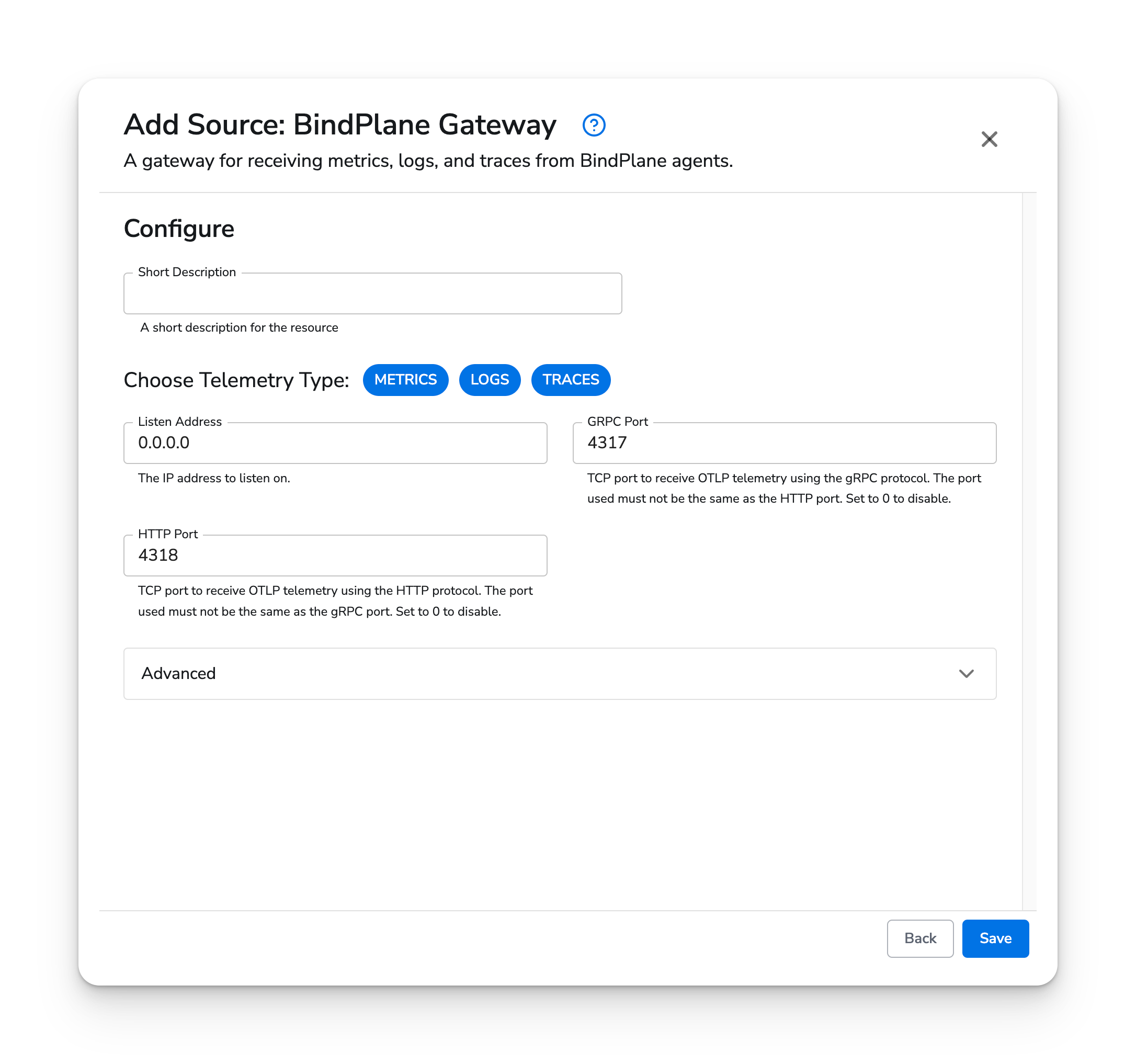
Kubernetes
The HTP Gateway source type supports Kubernetes, OpenShift Node (DaemonSet), and Gateway agents. Applications within the cluster can forward metrics, logs, and traces to the agents using the clusterIP services.Prerequisites
- Honeycomb Telemetry Pipeline v1.52.0 or newer
Configuration
The HTP Gateway source type does not require additional configuration. It can be attached to any Kubernetes, OpenShift Node (DaemonSet), or Gateway configuration. The following endpoints can forward telemetry to the managed Node (DaemonSet) agents.| Protocol | Service | Endpoint |
|---|---|---|
| gRPC | clusterIP | bindplane-node-agent.bindplane-agent.svc.cluster.local:4317 |
| gRPC | headless clusterIP | bindplane-node-agent-headless.bindplane-agent.svc.cluster.local:4317 |
| HTTP | clusterIP | http://bindplane-node-agent.bindplane-agent.svc.cluster.local:4318 |
| Protocol | Service | Endpoint |
|---|---|---|
| gRPC | clusterIP | bindplane-gateway-agent.bindplane-agent.svc.cluster.local:4317 |
| gRPC | headless clusterIP | bindplane-gateway-agent-headless.bindplane-agent.svc.cluster.local:4317 |
| HTTP | clusterIP | http://bindplane-gateway-agent.bindplane-agent.svc.cluster.local:4318 |