This feature is available as part of the Honeycomb Pro and Enterprise plans.
In this guide, we demonstrate a typical SAML Identity Provider configuration using Okta.
If you are using a different SAML Identity Provider, field names and locations may vary, so you will need to locate the corresponding fields in your Identity Provider’s user interface.
Before You Begin
To successfully complete this guide, you should have an active Okta account.Enable SSO in Honeycomb
To begin, enable SSO in Honeycomb, which will allow you to get Honeycomb’s Service Provider settings:- In Honeycomb, navigate to Account > Team Settings, and select the Team Details view.
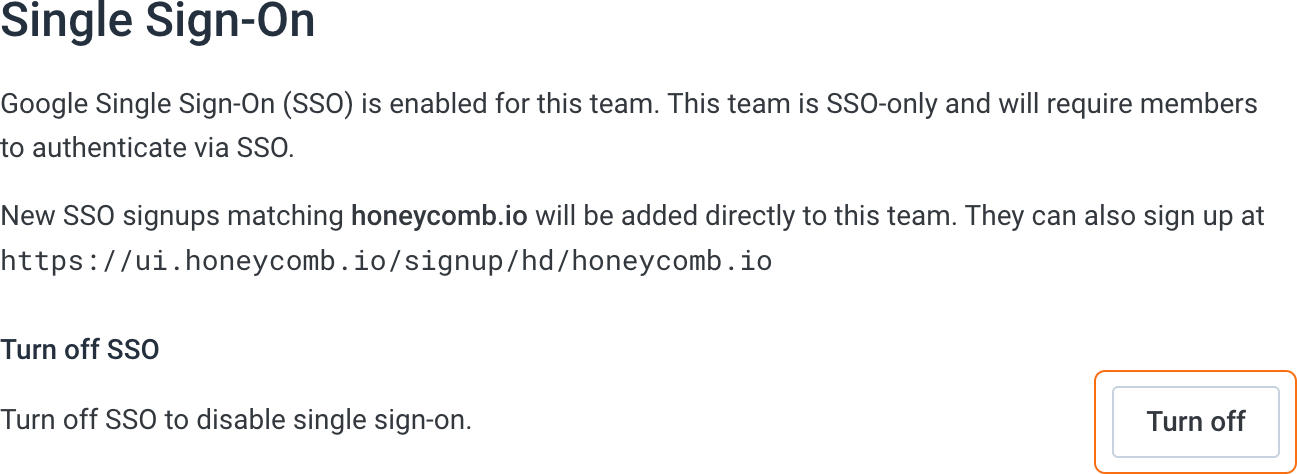
- Locate the Single Sign-On section, which displays any previous SSO configuration.
-
If your team is already configured to use Google SSO, turn off Google SSO.
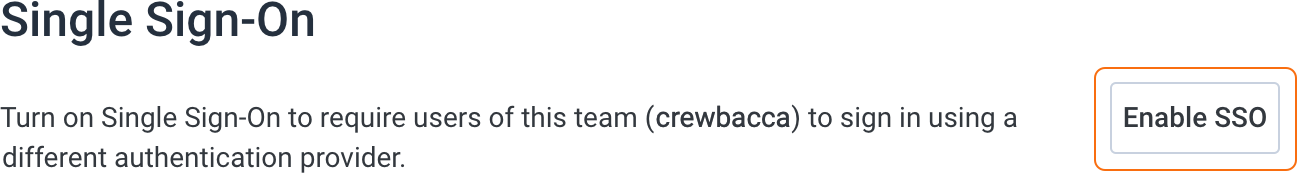
-
Select Enable SSO.
- In the SSO provider configuration modal, select SAML/Okta, then select Next.
-
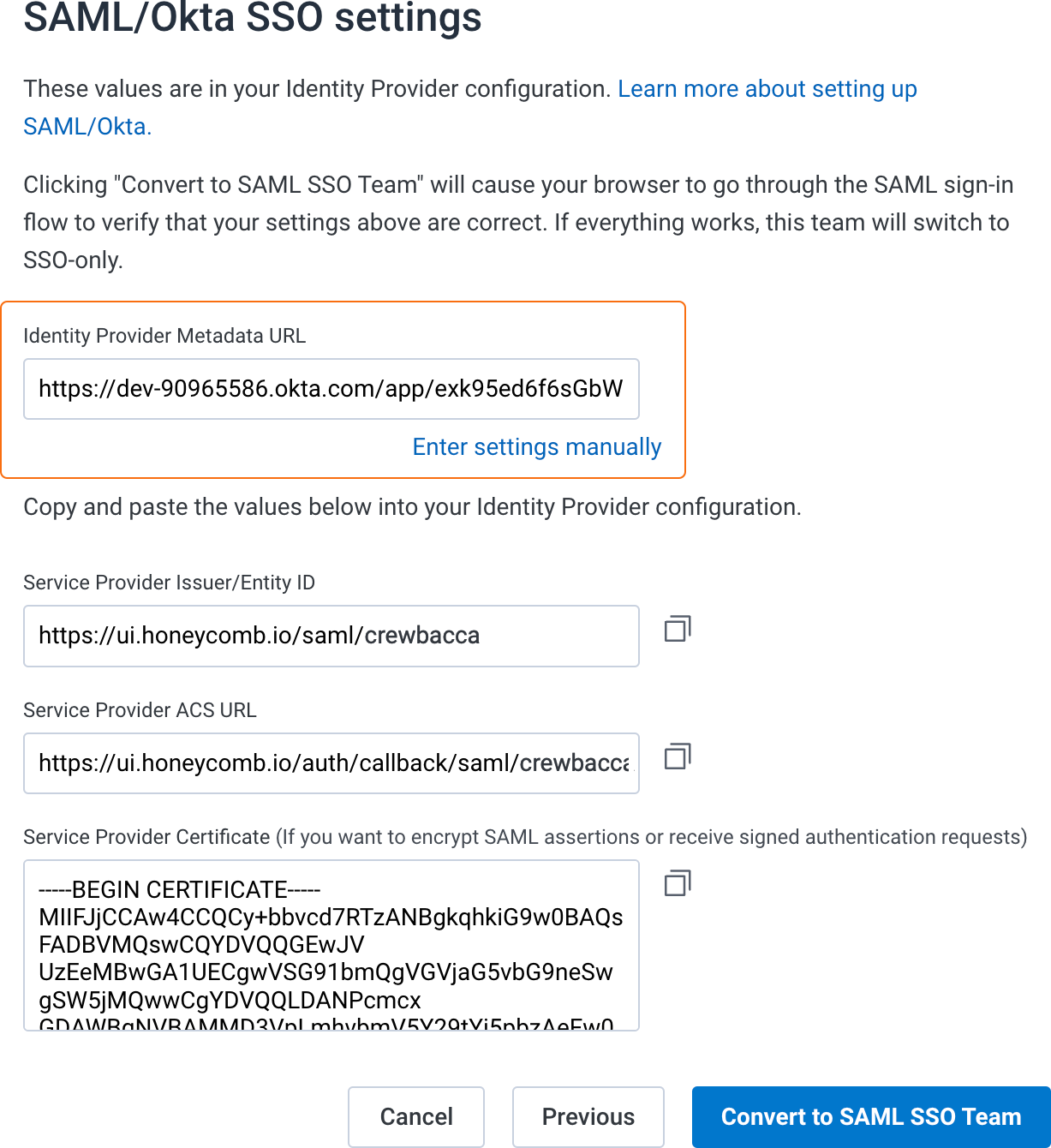
Locate the settings required by your Identity Provider. You will need:
- Service Provider Issuer
- Service Provider ACS URL
- Service Provider Certificate (optional, used when your Identity Provider requires encrypted SAML assertions or signed authentication requests)
 Honeycomb generates a unique identifier based on your team name. You will see the identifier appended to the values in the Service Provider Issuer and Service Provider ACS URL fields.For this example, the team name is “Crewbacca”, so the team’s generated identifier is
Honeycomb generates a unique identifier based on your team name. You will see the identifier appended to the values in the Service Provider Issuer and Service Provider ACS URL fields.For this example, the team name is “Crewbacca”, so the team’s generated identifier iscrewbacca.
Configure Your Identity Provider
Next, configure your Identity Provider to work with Honeycomb. To do this, you must set up SSO for an application integration in your Identity Provider, and then specify which users should be able to use SSO to log in to your team in Honeycomb.In this section, we demonstrate a typical SAML Identity Provider configuration using Okta.
If you are using a different SAML Identity Provider, field names and locations may vary, so you will need to locate the corresponding fields in your Identity Provider’s user interface.
Set Up SSO
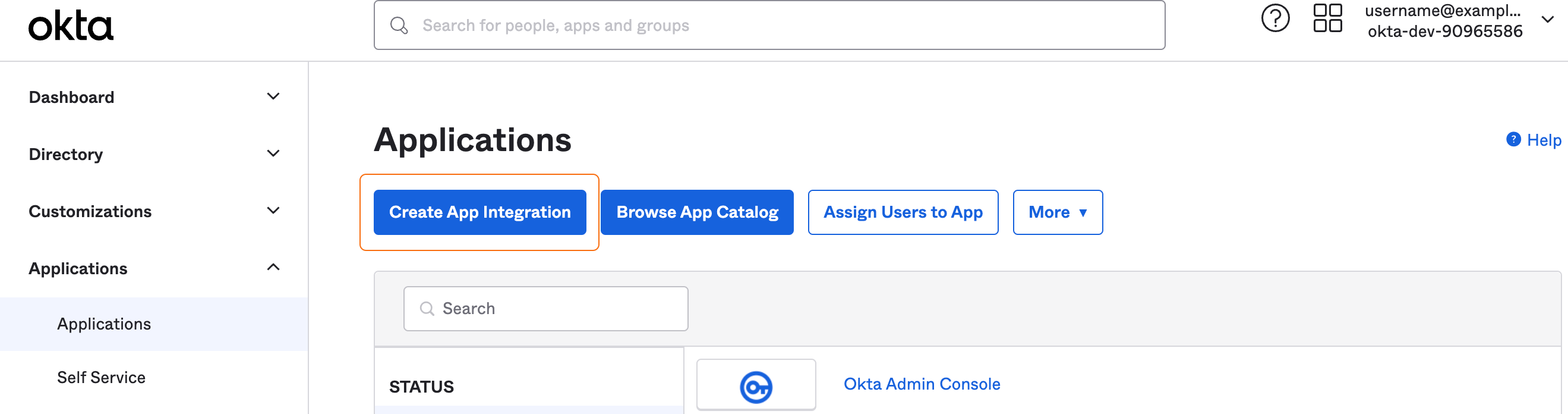
Set up SSO in your Identity Provider using the Service Provider settings you retrieved from Honeycomb:- Open a new browser tab, and go to your Okta admin console.
-
In Okta, go to Applications > Applications, and select Create App Integration.
- In the sign-in method modal, select SAML 2.0, then select Next.
-
For General Settings, locate App Name and enter a name for your application, such as in the format
Honeycomb [Your Team Name], then select Next. -
For Configure SAML, locate the SAML Settings section, and enter your retrieved Honeycomb setting values according to the following mapping:
Okta Field Honeycomb Setting Name Single sign-on URL Service Provider ACS URL Audience URI (SP Entity ID) Service Provider Issuer/Entity ID 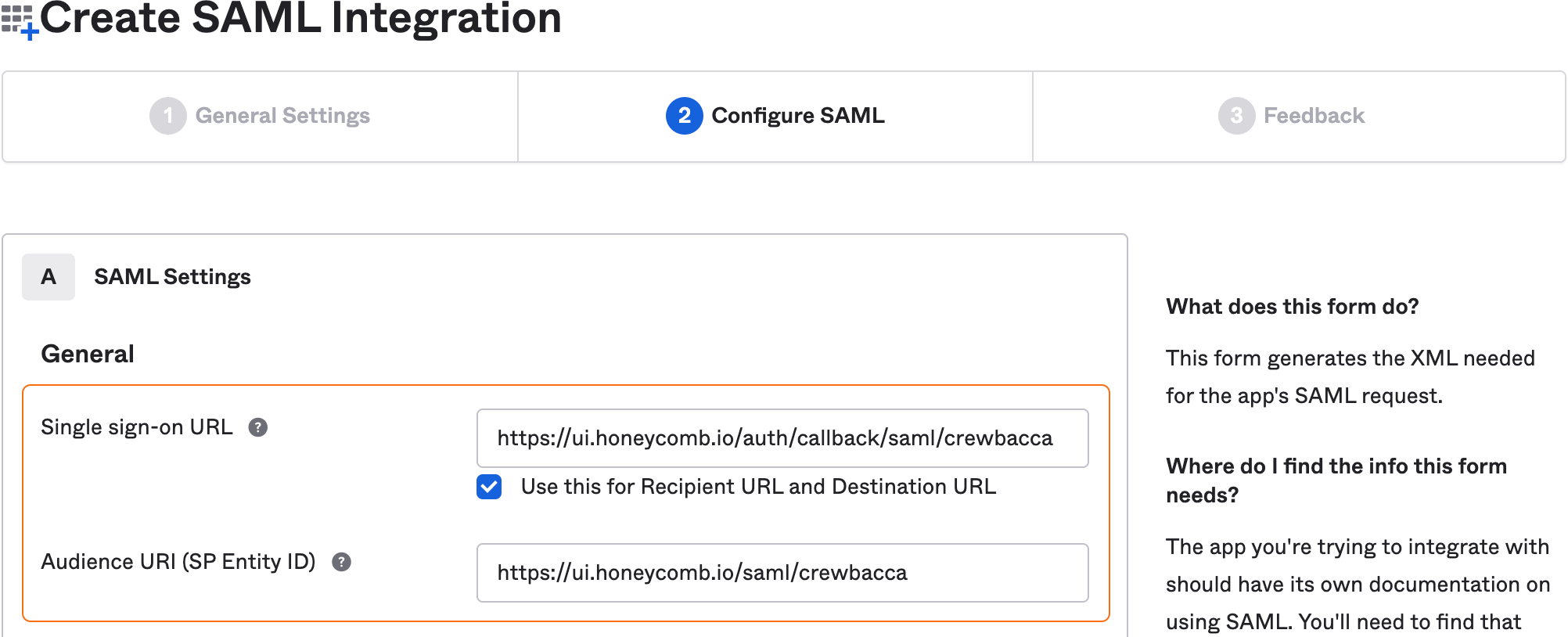
-
Locate the Attribute Statements section, and add the following exact values, then select Next:
The values for SAML attributes must be the exact values we provide below. For example, for the
Emailattribute, enteruser.email—not the actual email address of the user.Name Name format Value FirstNameUnspecifieduser.firstNameLastNameUnspecifieduser.lastNameEmailUnspecifieduser.email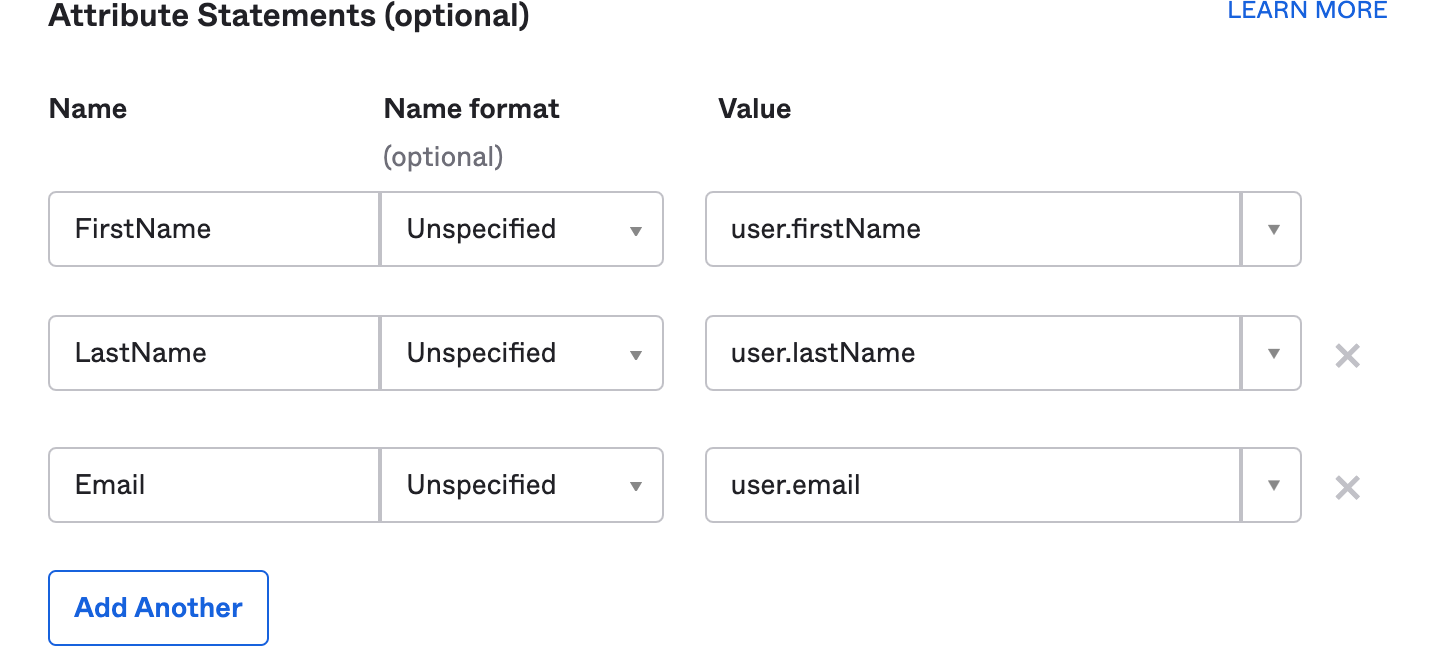
-
For Feedback, select the following values, then select Finish:
Field Value Are you a customer or a partner? I'm an Okta customer adding an internal appContact app vendor It's required to contact the vendor to enable SAML -
From the application’s SSO settings, locate and copy the Metadata URL. You will need this information to configure Honeycomb.
 Although most modern SAML Identity Providers, like Okta, provide a Metadata URL, not all do. If your Identity Provider does not provide a Metadata URL, you must locate the required information to configure Honeycomb. Information you need includes:
Although most modern SAML Identity Providers, like Okta, provide a Metadata URL, not all do. If your Identity Provider does not provide a Metadata URL, you must locate the required information to configure Honeycomb. Information you need includes:- Identity Provider Issuer
- Identity Provider SSO URL
- Identity Provider Certificate (optional, used when your Identity Provider requires signed authentication requests)
Assign Users
Assign users to the Honeycomb application in your Identity Provider:To finish your Honeycomb configuration, you must assign your own user account to the Honeycomb application in your Identity Provider. If you want, you can wait and add more users later.
- Go to your new application, and select the Assignments view.
-
Select Assign > Assign to People or Assign to Groups, depending on whether you want to allow individual users or specific groups to log in to your team in Honeycomb.
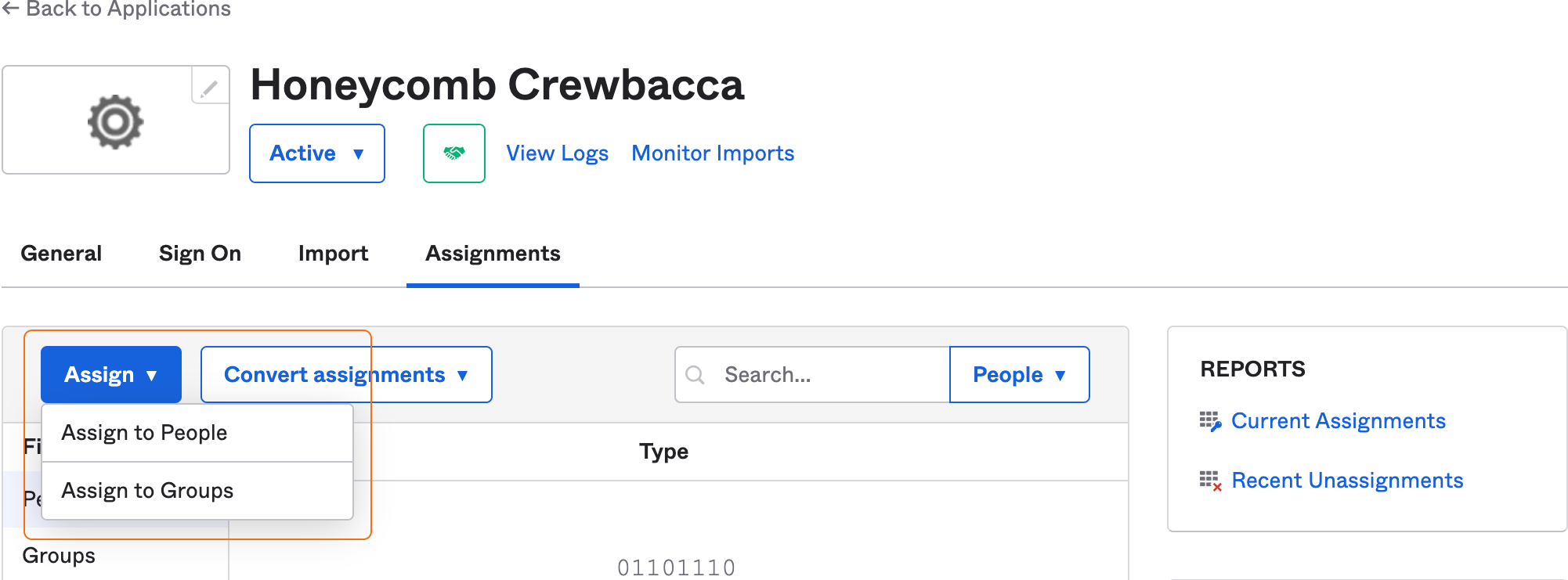
- In the group assignment modal, search for and select Assign next to the individual users or specific groups you want to allow to log in to your team in Honeycomb using SSO, then select Done. Remember to assign your own account to the application.
- Confirm that the Assignments view reflects your selections.
Configure Honeycomb
Finally, configure SSO in Honeycomb using the Identity Provider settings you retrieved from your Identity Provider. Some Identity Providers, like Okta, provide a metadata URL, which allows Honeycomb to fetch the settings it needs and update them automatically. Other SAML Identity Providers may not provide metadata URLs. If your Identity Provider does not provide a metadata URL, you must configure Honeycomb manually and maintain its configuration settings.- Configure Honeycomb Automatically
- Configure Honeycomb Manually
If your Identity Provider provided a metadata URL, like Okta does, automatically configure SSO in Honeycomb:
- Switch to the browser tab that contains your Honeycomb Service Provider settings, locate the Identity Provider Metadata URL, and paste the metadata URL you copied from your Identity Provider.
-
Select Convert to SAML SSO Team.